Best Hacks and Tricks That You Can Perform On Kali Linux – Kali Linux is a Debian-based Linux dissemination went for cutting edge Penetration Testing and Security Auditing. Kali contains a few hundred devices which are adapted towards different data security undertakings, for example, Penetration Testing, Security look into, Computer Forensics and Reverse Engineering. Kali Linux is produced, supported and kept up by Offensive Security, the main data security preparing organization. And this is the only operating system where you can perform lots of hacks like below.
Hacks To Perform on Kali Linux
1 Wash
- Wash is an instrument to figure out if a get to point has WPS empowered or not.
- You can likewise utilize Wash to check if a get to point bolted up WPS after various Reaver endeavors.
- A great deal of getting to focuses locks itself up as a safety effort when Savage is driving the WPS PIN.
- Wash is incorporated with the Reaver bundle and comes as a standard apparatus with Kali Linux.
2 Pixiewps
- PixieWPS is a new device included with Kali Linux and furthermore, focuses on a WPS helplessness.
- PixieWPS is composed of C and is utilized to animal constrain the WPS PIN disconnected misusing the low or non-existing entropy of helpless get too focused.
- This is known as a tidy pixie assault. PixieWPS requires an adjusted rendition of Reaver or Wifite to work with.
3 Wireshark
- Wireshark can be utilized for live parcel catching, profound assessment of several conventions, peruse and channel bundles and is multiplatform.
- Wireshark is incorporated with Kali Linux additionally accessible for Windows and Mac.
- For specific elements, you do require a Wifi connector which is backings indiscriminate and observing mode.
4 oclHashcat
- oclHashcat is not a committed Wifi hacking apparatus and is excluded with Kali Linux, but rather it can do beast constrain and lexicon assaults on caught handshakes quick when utilizing a GPU.
- In the wake of utilizing the Aircrack-ng suite, or some other apparatus, to catch the WPA handshake, you can break it with oclHashcat utilizing your GPU.
- Utilizing a GPU with oclHashcat, rather than a CPU with Aicrack-ng, will accelerate the splitting procedure a great deal.
- A normal GPU can attempt around 50.000 blends for each second with oclHashcat.
- oclHashcat is accessible for Windows and Linux and has a form for AMD and Nvidia video cards. AMD video cards require Catalyst 14.9 precisely, and Nvidia video cards require ForceWare 346.x or later to work.
5 Aircrack-ng
Aircrack is a standout amongst the most common instruments for WEP/WPA/WPA2 splitting. The Aircrack-ng suite contains apparatuses to catch parcels and handshakes, de-confirm associated customers and produce activity and instruments to perform beast compel and word reference assaults. Aicrack-ng is an across the board suite containing the accompanying devices (among others):
- Aircrack-ng for remote secret key breaking
- Aireplay-ng to produce activity and customer de-confirmation
- Airodump-ng for parcel catching
- Airbase-ng to arrange fake get to focuses
The Aicrack-ng suite is accessible for Linux and comes standard with Kali Linux.
6 Crunch
- Crunch is an extraordinary and simple to utilize instrument for creating custom word lists which can be utilized for lexicon assaults.
- This component can spare a great deal of time since you won’t need to hold up until extensive secret key records have been created by Crunch before you can utilize them.
7 Wifite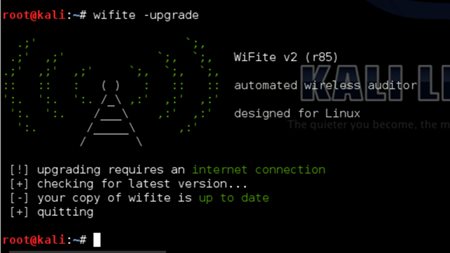
- Wifite is a robotized instrument to assault various remote systems scrambled with WEP/WPA/WPA2 and WPS.
- On start-up, Wifite requires a couple of parameters to work with, and Wifite will do all the diligent work.
- It will catch WPA handshakes. Naturally, de-confirm associated customers, parody your MAC address and safe the split passwords.
8 Macchanger
- Macchanger is somewhat utility which can be utilized to parody your MAC deliver to an irregular MAC address, or you can make up your own.
- Mocking your MAC address for wifi hacking may be vital keeping in mind the end goal to maintain a strategic distance from MAC channels or to veil your character on a remote system.
- Macintosh Address satirizing with mac changer
9 Reaver
- Reaver is another famous instrument for hacking remote systems and targets particularly WPS vulnerabilities.
- Utilizing Reaver requires a decent flag quality to the remote switch together with the correct arrangement.
- Overall Reaver can recuperate the passphrase from defenseless switches in 4-10 hours, contingent upon the get to point, flag quality and the PIN itself off base.
- You have a half possibility of breaking the WPS PIN in half of the time.
10 Fern Wifi Cracker
- Plant Wifi Cracker is a remote security inspecting and assault instrument written in Python. Plant Wifi Cracker is the initially devoted Wifi hacking device in this rundown which has a graphical UI.
- The plant can split and recuperate WEP, WPA and WPS keys and contains instruments to perform MITM assaults.
- Greenery Wifi Cracker keeps running on any Linux circulation which contains the essentials. Plant Wifi Cracker is incorporated with Kali Linux.