Hacking has become so ritualistic in our lives that there is only a thin line left between white-hats and black-hats. The endeavors of safety professionals require high precision skills to remain one up on data safety and fortifying all the vulnerable spots for unwanted intrusion.
Hacking requires the backing of top hacking tools to do their jobs perfectly. The MAC devices are still hacked, although Apple claims a solid defense line against hacking. There are many online open source tools to hack Mac devices.
Here are top ten ethical hacking tools in 2017 for MAC.
1. Network Mapper(Nmap):
This tool finds all connected devices and IPs and determines the OS of host connected to network. It is preinstalled on Kali Linux and used to hack MAC devices also.
2. Metasploit:
An outstanding hacking tool, it is used for making a customized tool for penetration testing. It can detect vulnerabilities on different OS. This is an open source tool that can be downloaded to MAC.
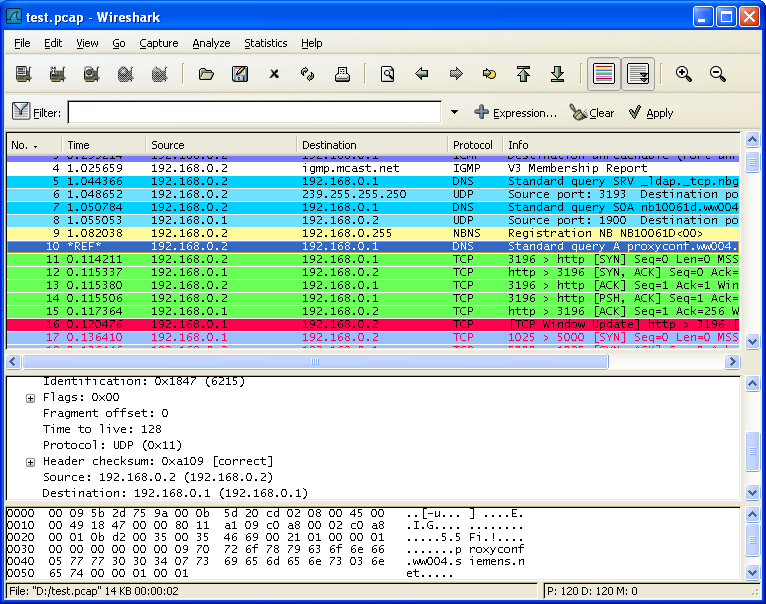
3. Wireshark:
Wireshark monitors network and analyzes all sent or received data packets. Passwords, personal information can be sniffed. Wireshark is one of the most popular tool in networking.
4. Social Engineering Toolkit(SET):
It is measured one of the best tool for password cracking, phishing and, social attacks. It can do SMS and Emails bombing to frustrate others, it is written in Python.
5. Aircrack-ng:
It is capable of hacking into Wi-Fi and determine password, and checks network security. It is a powerful tool and is used widely across the world.
6. John the Ripper:
Is used to find passwords in hashes like Crypt, MD%. It can also make dictionary attacks which is a list of passwords or a dictionary file.
7. Driftnet:
All images being transmitted or received on a network are detected by Driftnet and are displayed on the screen. It comes preloaded on Kali Linux, on MAC it can be downloaded.
8. SSL Strip:
If complete traffic is required on HTTP instead of HTTPS, SSL Strip is a very handy tool. It diverts all the traffic to the unsecured connection making it easier to access information.

9. MdK3:
MdK3 creates self-data packets, and send de-authentication request to networks, resulting in crash of all networks. Security is its key feature.
10. Burp Suite:
For performing security testing with web applications, this tool is used. It does everything like initial mapping, analysis of an application’s attack surface, locating and exploiting the security vulnerabilities.
Word of caution-
Majority of these tools can crack the network passwords but the time taken depends upon the password chosen. A complex and lengthy password may take much longer vis-a-sis a simple one. Some tools may not be effective in direct use. In that case a packet analysis helps in guessing the password.
Be careful to use these strictly for learning purposes only and not to indulge in any unethical or illegal activities. It is a cyber-crime to hack a wireless network and access a network to steal important personal sensitive information.