Hackers are always ready to pounce on any detected vulnerability in the targeted devices. Cross Site Scripting (XSS or CSS) is a known vulnerability in web applications. There are many types of XSS invasions that means a hacker injects certain code into web applications to break through the security of device. This is the favorite route that hackers take to intrude the devices.
Types of Cross-Site Scripting
The three types of Cross-Site Scripting that are commonly used viz., DOM-based XSS, Non-persistent XSS, and Persistent XSS.
DOM-based XSS-
Document Object Model (DOM) based XSS attack changes and modifies DOM so the client’s device runs according to the changed version. The hackers exploit HTML pages in the devices, when they find any code vulnerability.
The attacker achieves multiple results with DOM-based XSS attack. Hacker can create a malicious website, and then it sends commands to vulnerable HTML pages that execute the command and use the owner’s device for own benefit. The hacker through this attack takes command of the targeted device.

Non-Persistent XSS-
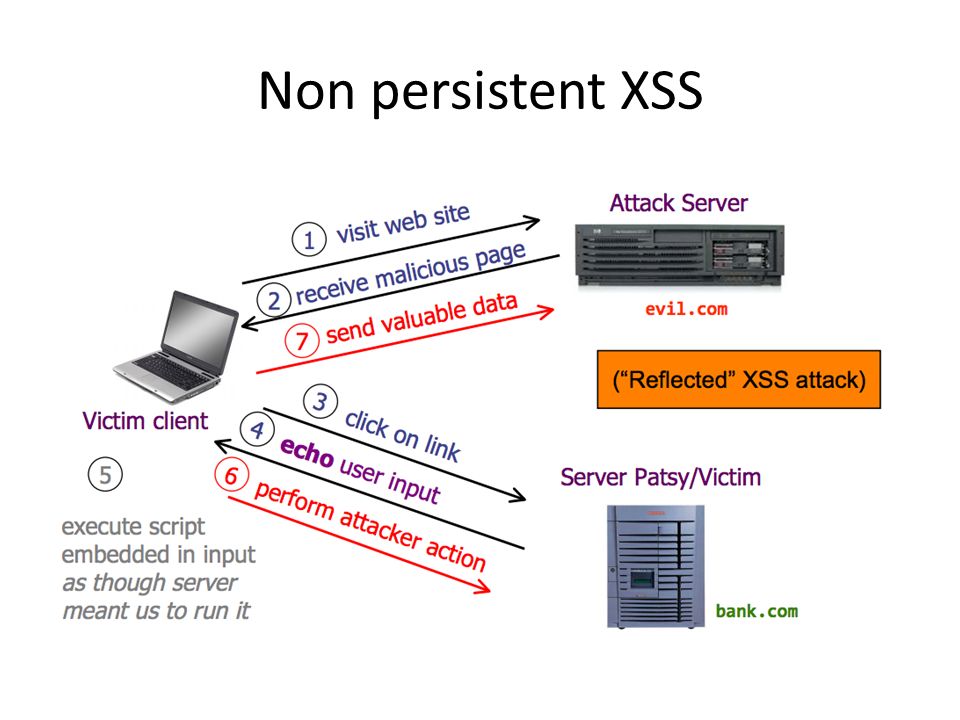
Most common of vulnerability found on the net is non-persistent XSS, named so because it is promptly responds to HTTP of the targeted device. Also known as Reflected XSS, it works on the targeted victim’s ignorance that sends malicious code to web application. It is reflected on victim’s browser where XSS attack takes over the device with its malicious load. This operation is carried out in one-shot request.
Persistent XSS-
The third wing of XSS attacks is Persistent XSS, itacts when web application stores user participation sends back to other users without validation on HTML response pages. Thus, the attackers inject malicious code into vulnerable web pages and store it on the web server for later use. Unlike Non-Persistent XSS, Persistent gets in the vulnerable web page and access all that the user has there.
Persistent is less common than other two, as this looks to attack within certain rare vulnerabilities. But this is rather more damaging to the web device as when payload is off-loaded in the system. It contaminates other data also for hacker’s benefit. This is known to affect the visitors too that visit the website. This is also known as Type2 XSS as it works on two methods; first for inserting malicious code and storing that on web server. The other one, when victim loads infected HTML pages.
XSS prevention
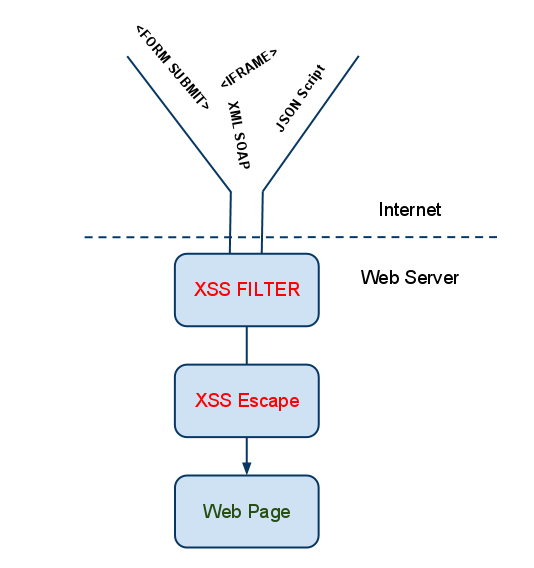
The prevention of XSS for security experts is a big challenge as this hacking attack is very potent. Still there are few ways one can put on some resistance or look for the preventive ways.
Encoding of Output–
Output-encoding works well on server generated pages and it works well to counter the XSS payloads. HTML is a common encoding to check XSS attack to make any malicious marks. URL encoding helps to neutralize the payload offloaded on links and redirects.
Then the content security policyhas useful settings that include log violations that are indicative enough for XSS attack attempts on the site.